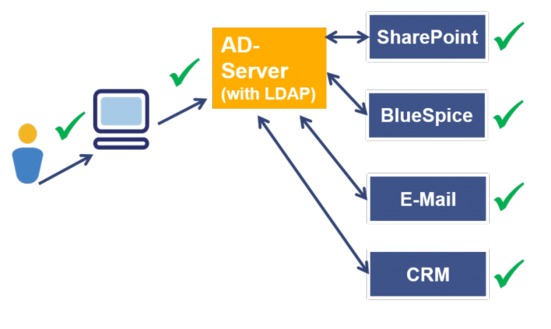
Authentication with LDAP
-
- Last edited 5 years ago by MLR
-
-
- This page is approved but has a draft version
LDAP means Lightweight Directory Access Protocol. This can be used for centralized authentication. This extension allows you to connect BlueSpice (and MediaWiki) to an LDAP server for central authentication.
Important!
Due to a security vulnerability in Active Directory, the use of a secure connection (with SSL / TLS encryption) for user authentication is strongly recommended.
A Microsoft patch for March 2020 no longer allows unsecured connections:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV190023
https://support.microsoft.com/en-us/help/4520412/2020-ldap-channel-binding-and-ldap-signing-requirement-for-windows
Any software that makes LDAP queries over unsecured connections is affected. Depending on the settings, this may also affect BlueSpice MediaWiki. If your system is configured to already use a secure connection, there is nothing you need to do.
If BlueSpice and Active Directory communicate via an unsecured connection, the system must be reconfigured to remain accessible.
Please check your configuration and contact us if you have any questions.
Contents
BlueSpice with LDAP
The MediaWiki extension "LDAP Authentication" is available in BlueSpice free, but is not activated by default. To link the Wiki to LDAP you need to activate the extension and configure it.
Configuration options
| LDAP | Connection to AD without group synchronization |
| LDAP with group synchronization |
If you have already defined user groups for your company, they can be adopted for the wiki. The corresponding groups are automatically present in the wiki with the group name and you can assign the corresponding rights to the groups there. |
| Comfort Sign-on | such as LDAP with group synchronization as above To further extend the connection to a central authentication, there is the possibility to set up a single sign-on. This means that the user is also logged on to the wiki at the same time when logging on to the PC. |
Please note after configuring LDAP
- The wiki does not write back to the LDAP directory.
That means, e.g. password changes in the wiki can lead to a conflict with the AD. In the best case, the changes will be overwritten by LDAP during the next login. - It is not allowed to create users manually in the wiki. This leads to the conflict, even if the convention of the LdapAuthentication is case-sensitive.
- No users can be created in the LDAP directory via UserManager in the wiki.
- By default, there is no initial and / or active synchronization with the LDAP directory. Users do not appear until after the first login in the wiki.
- A group assignment is possible via the wiki.
LDAP configuration with group synchronization also applies:
- Again, the AD is the leading authority, Groups are taken over from the AD.
Caution: The corresponding group must be created with the identical name, as it is called in the AD directory, in the group manager of the wiki in order to guarantee the group assignment. - Groups can not be assigned to the user manually in the wiki. Please make the assignment via the LDAP directory.
- Groups that a user does not belong to in the LDAP directory are not displayed in the wiki.
- The assignment of the user to groups takes place during the login routine with the respective user, also here: no automatic comparison with the directory in the background.
- A group assignment via the wiki is not possible. Exceptions are the groups sysop, bot and bureaucrat. These can be assigned via the wiki and are not withdrawn from the user.
LDAP configuration with Comfort Sign-on also applies:
- Browser requirements: compatability with Internet Explorer, Edge und Google Chrome
- Security requirement: https, not http
- The web page must be assigned according to the local intranet (group guideline)